⚡ Tl;dr
- System and Organizational Controls (SOC) is a suite of examinations performed by an accredited auditor which can be used by existing or prospective customers to assess and identify risks for an outsourced service.
- SOC 1 is for services that store financial user data, SOC 2 is for services that store sensitive user data, and SOC 3 is a SOC 2 report re-written for a general audience.
- We use Vanta for our SOC 2 Type 2 compliance which allows us to automate technical controls, upload evidence for manual controls and manage our policies, risk assessments, SLAs and inventory.
🚀 Let’s kick-off
When selling B2B software, it can be challenging to demonstrate your security and compliance when approaching larger enterprises. It’s critical to gain their trust and assure them that you’re handling their sensitive data in line with regulations and industry best practices. Data breaches are becoming increasingly frequent and have increased by 14% between 2021 and 2022, as the Identity Theft Resource Centre (ITRC) reported. An IBM report in 2022 puts the average cost of a US data breach at $9.44 million, which can be devastating for the companies affected.
Most companies with InfoSec processes require vendors to complete lengthy security questionnaires OR provide a security compliance report; sometimes both. Filling out these security questionnaires can be time consuming and challenging as each can differ wildly from the next. We completed many of these questionnaires in the early days at IcePanel and soon looked for better ways to assure our customers that we secure and protect their data.
We decided to become SOC 2 Type 2 compliant, and here’s what we learnt from the process.
🔐 What is SOC?
System and Organizational Controls (SOC) is a suite of examinations defined by AICPA and can be used by existing or prospective customers to assess and identify risks for an outsourced service. The resulting report provides assurance about the service organization’s ability to design and operate controls which meet the objectives defined by AICPA. Only AICPA-affiliated CPAs (Certified Public Accountants) can perform SOC audits and issue a report.
There is a common misunderstanding about the correct terminology for becoming SOC compliant/certified. A quick Google search reveals websites, blog articles and social media posts discussing their SOC certification. However, there is no SOC certification; the correct terminology is SOC compliance or attestation. We’re also guilty of this mistake.
Once the SOC report has been issued, you can use the official SOC for service organizations logo on websites, social media, presentations or printed media to assure users of your security practices. The logo can only be used in the period that the report is effective, which is usually 12 months.
📄 SOC reports
SOC 1
The SOC 1 report is for service organizations that store, process, or transmit sensitive financial information about their users, such as loan or insurance providers. It assures customers about the internal controls and processes to perform financial reporting.
The type 1 report covers the suitability of controls and how well they achieve the control objectives at a specific point in time. The type 2 report extends this to cover the effectiveness of those controls over a specific audit period.
The information included in this report is classified and should only be distributed to those who have signed a non-disclosure agreement (NDA).
SOC 2
The SOC 2 report is for a broader range of service organizations that store, process, or transmit sensitive user data. It assures customers about the internal controls and processes relating to the system’s Trust Services Criteria, which include security, availability, processing integrity, confidentiality and privacy. Trust Services Criteria apply to the service organizations infrastructure, software, people, procedures and data.
Like SOC 1, the type 1 report covers controls at a specific point in time, and the type 2 report extends this over a specific audit period.
The information included in this report is classified and should only be distributed to those who have signed a non-disclosure agreement (NDA).
SOC 3
The SOC 3 report is an extension of SOC 2 and is essentially the same report and assurance but rewritten for a more general audience. Readers don’t need to know how to understand the complex SOC 2 report structure.
SOC 3 reports can be freely distributed as they do not contain sensitive information.
✅ SOC 2 Type 2
Let’s discuss what we needed for our SOC 2 Type 2 compliance audit and how the report was structured. Our audit was performed by Prescient Assurance, who audited us for three months.
System description
The SOC 2 report includes a system description which gives a high-level overview, sets the scope for the audit and is written by the service organization. It provides information about the company, product, system and security, allowing existing and potential customers to complete their assessment of the service organization.
Testing matrices
In this section, the auditor describes the testing and sampling methodologies they used to complete the audit. This covers how many items need testing per control and how frequently they need testing.
Controls
This part of the report lists each control with a short description of the evidence the auditor reviewed to support it. The auditor will note exceptions during the audit window for any controls and sometimes a response from management about improvements being made to prevent the control from failing again.
A large number of controls relate to having effective policies and processes in place within the business. We tested some of our policies in a discussion, such as with our incident response plan and disaster recovery plan.
We included the following policies as part of our audit:
- Access Control Policy
- Asset Management Policy
- Business Continuity and Disaster Recovery Plan
- Code of Conduct
- Cryptography Policy
- Data Management Policy
- Human Resource Security Policy
- Incident Response Plan
- Information Security Policy (AUP)
- Information Security Roles and Responsibilities
- Operations Security Policy
- Physical Security Policy
- Risk Management Policy
- Secure Development Policy
- Third-Party Management Policy
There are engineering tasks involved with ensuring that our technical systems are secure. Many of these are easily automated to assure the auditor that it was performed correctly throughout the audit window.
We looked at some of the following areas as part of our audit:
- Minimum authentication and password requirements such as 2FA and practicing the principle of least privilege.
- Automated vulnerability scanning and patching vulnerabilities within our specified SLAs.
- Annual penetration testing and resolving vulnerabilities within our specified SLAs.
- Encryption, network segmentation, intrusion detection and access restriction/reviews on our production environment.
- Infrastructure log management, performance monitoring and alerting on our production environment.
- Software and hardware inventory management and vendor review.
- Change management procedures.
We had controls relating to the product and service offering, which required us to have the following available:
- Website communicating our product offering.
- Support system available for users to report issues, incidents or concerns.
- Status website communicating system availability.
- Documentation website offering help and guides for users.
- Security page showing our commitment to security.
- Changelog for externally communicating system changes.
We completed risk assessments in the following areas and performed tasks to mitigate the recorded risks.
- Sensitive data
- Codebase
- People
- Production services
- Physical security
- Fraud
The last major area was ensuring we perform management and employee processes which include:
- Onboarding and offboarding employees within our specified SLAs.
- Revoking access for terminated employees within our specified SLAs.
- Employee background checks and performance evaluations.
- Employee security awareness training.
- Organization structure maintained and management roles defined.
- Management meetings were conducted with minutes.
🤖 Automating compliance
There are tools for automating compliance which saved us a huge amount of time for preparing and during our audit. We connected our tooling to Vanta, which provides a list of tasks to become compliant and periodically checks for passing/failing controls. Vanta also gave us a platform to manage our policies, risk assessments, SLAs, inventory, employees, security awareness training and vendors, allowing us to become compliant in just a few weeks.
During our audit, we ensured that all automatic checks were passing consistently and uploaded evidence for controls that could not be tested automatically. Once the 3-month audit window was complete, our auditor used the automated checks and manually submitted evidence in Vanta to assert that our controls were implemented correctly and passed for the whole period. Our auditor then spent a couple of weeks writing up the finalized report.
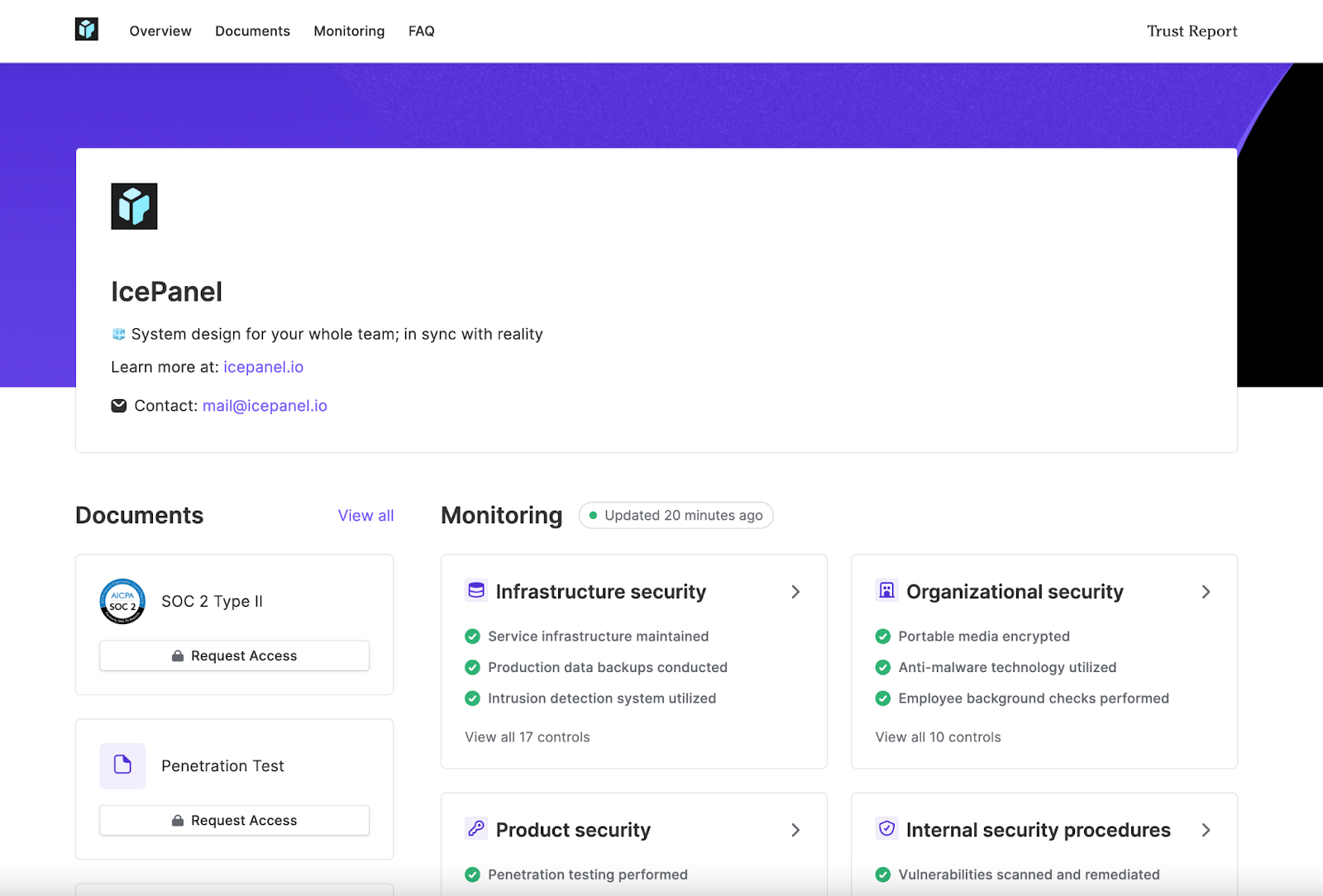
Receiving our 80-page audit report after six months of work was amazing for us. We hope this can assure our customers that we’re investing in our security practices to ensure we keep their data safe. After receiving our report, we uploaded it to our Vanta trust report, allowing our existing and prospective customers to access our SOC 2 Type 2 and penetration test reports. This makes it super simple to get NDA acceptance and allows downloading the reports they need. Real-time checks are also available here for all the controls that Vanta monitors for us.
🏁 To wrap up
Looking back, it was an expensive and time-consuming process to complete our SOC 2 Type 2 compliance. However, we believe it was worth the investment. We identified and resolved some gaps in our security and process while preparing for the audit, and we will continue to ensure that we stay compliant moving forwards.
We hope this gives our existing and prospective customers peace of mind that we’re investing in our security practices.
Stay chill 🧊
